Fake CAPTCHA (ClickFix) Attack Chain Leads to Enterprise‑Wide Malware Infection in Organisations
3 min read
A sophisticated cyberattack campaign leveraging “ClickFix” social engineering has emerged, posing a severe threat to enterprise networks globally.
These massive campaigns, which trick users into executing malicious code under the guise of resolving a fake technical error, have become increasingly prevalent.
Recently, a large Polish organization fell victim to this scheme, demonstrating how a single user’s error can compromise an entire corporate infrastructure.
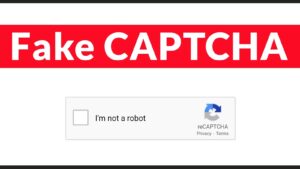
The attack vector is distinctively deceptive. Users visiting compromised websites encounter a fake CAPTCHA or error verification prompt, often mimicking Google Chrome or Microsoft Word interfaces.
This prompt instructs the victim to “fix” the issue by copying a specific PowerShell script and executing it manually via the Windows Run dialog (Win+R).
By relying on the user to actively execute the code, the attackers successfully bypass standard browser security protections and automated download filters.
.webp)
Upon execution, the pasted script downloads a dropper that initiates the infection chain. Cert.pl analysts identified the malware after the second paragraph of their investigation, noting suspicious traffic originating from the compromised host.
Their analysis revealed that the initial PowerShell command retrieves a malicious payload from a remote domain, effectively establishing a foothold within the network.
The researchers emphasized that while the initial vector relies on user interaction, the subsequent automated stages are rapid and difficult to arrest without robust behavioral monitoring.
The impact of this infection is critical, often leading to enterprise-wide compromise. The attackers use the initial access to deploy secondary payloads, such as the Latrodectus and Supper malware families.
These tools facilitate data exfiltration, lateral movement, and potential ransomware deployment.
The ability to proxy traffic through the infected machine allows threat actors to map the internal network stealthily, identifying critical assets for encryption or theft.
Infection Mechanism and Evasion Tactics
The malware employs advanced evasion techniques, primarily relying on DLL side-loading to mask its presence.
In the analyzed incident, attackers dropped a legitimate igfxSDK.exe executable alongside a malicious wtsapi32.dll file in the %APPDATA%Intel directory.
When the legitimate application launches, it automatically loads the malicious library, allowing the code to execute within the context of a trusted process.
This technique effectively hides the malicious activity from many basic endpoint detection solutions. Furthermore, the identified Latrodectus variant utilizes significant anti-analysis mechanisms.
It performs NTDLL unhooking to remove monitoring hooks placed by antivirus software, blinding security tools to its activities. The malware also checks for sandbox environments and refuses to execute if launched by standard system tools like rundll32.exe.
Recommendations include blocking the execution of unverified scripts, monitoring for unusual PowerShell activity, and educating employees about the dangers of “fixing” browser errors via the Run dialog.
Network administrators should also block known Command and Control (C2) IP addresses associated with Supper and Latrodectus.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.
The post Fake CAPTCHA (ClickFix) Attack Chain Leads to Enterprise‑Wide Malware Infection in Organisations appeared first on Cyber Security News.
Kaynak: Cyber Security News
Yayin Tarihi: 18.02.2026 18:30